To enhance the security of our Active Insite server in Santa Fe, New Mexico, we initially relied on a paid firewall service from Cisco. While this solution offered reliable off-the-shelf protection, we sought more functionality, no recurring fees, and the flexibility of a Linux-based firewall distribution. After careful consideration, we chose IPFire, an open-source firewall solution that met our needs perfectly. Learn more about IPFire here. To run IPFire, we needed suitable hardware. Any computer with multiple network cards can be configured, or existing firewall hardware can be repurposed. We opted to install IPFire on a refurbished Sophos XG135 firewall unit, upgrading its memory to ensure optimal performance.

IPFire firewall OS enables comprehensive traffic monitoring and offers advanced tools for securing our internet connection, which is essential for our New Mexico-based company that operates solely within the United States. While our business focus is domestic, effective internet traffic management and SEO optimization require us to consider connections from key international locations such as Germany, Canada, and the Netherlands. These countries host important servers that contribute to our overall SEO strategy.
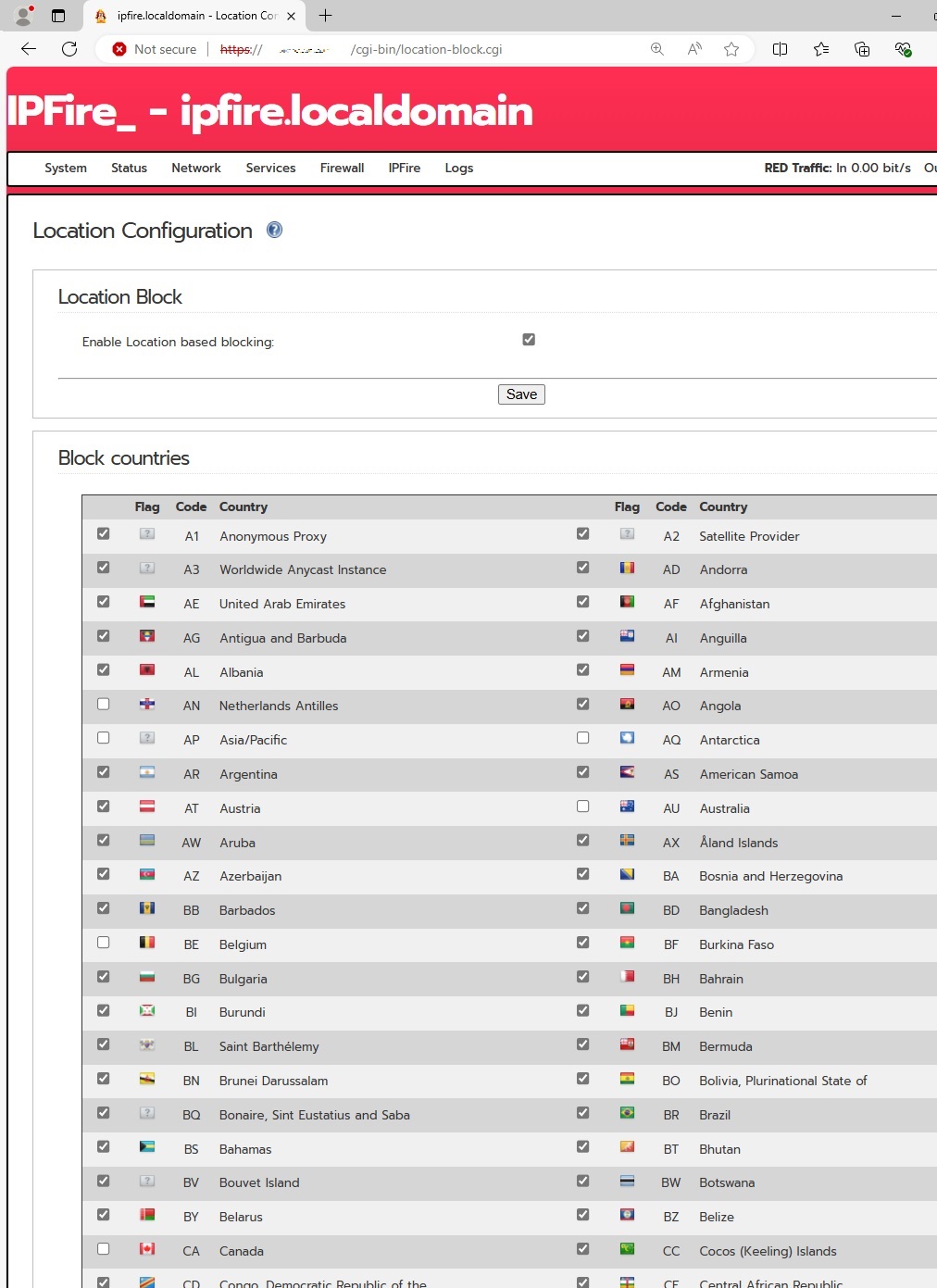
After allowing traffic from these key locations, we implemented strict rules to block traffic from all other regions. Although maintaining some global SEO traffic is important, the persistent hacking attempts from high-risk regions, particularly Russia and parts of the EU, made it necessary to enforce more stringent security measures.
Following the implementation of these traffic blocks, we observed a marked decrease in firewall hits, demonstrating the effectiveness of these enhanced security protocols.
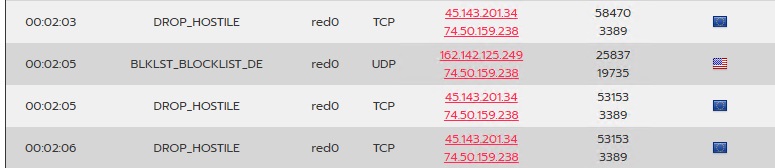
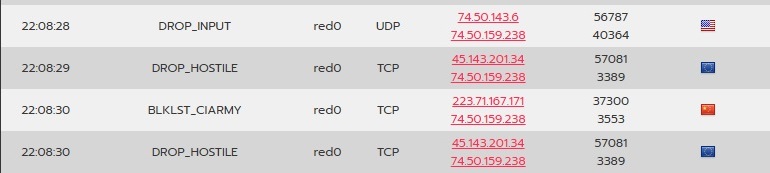
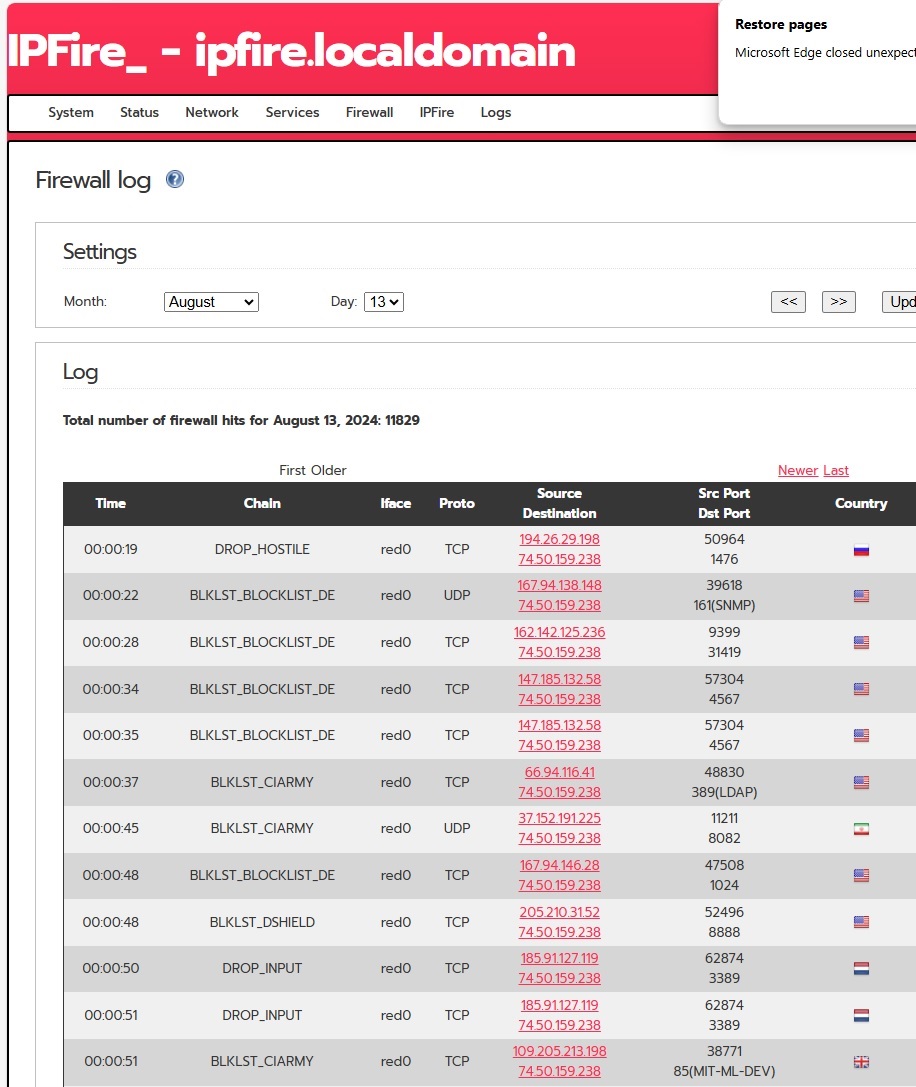
IPFire's botnet/bad actor blocklist automatically drops connections from
known malicious IP addresses. Before enabling any blocklist rules,
our server experienced nearly 73,000 firewall hits in one day,
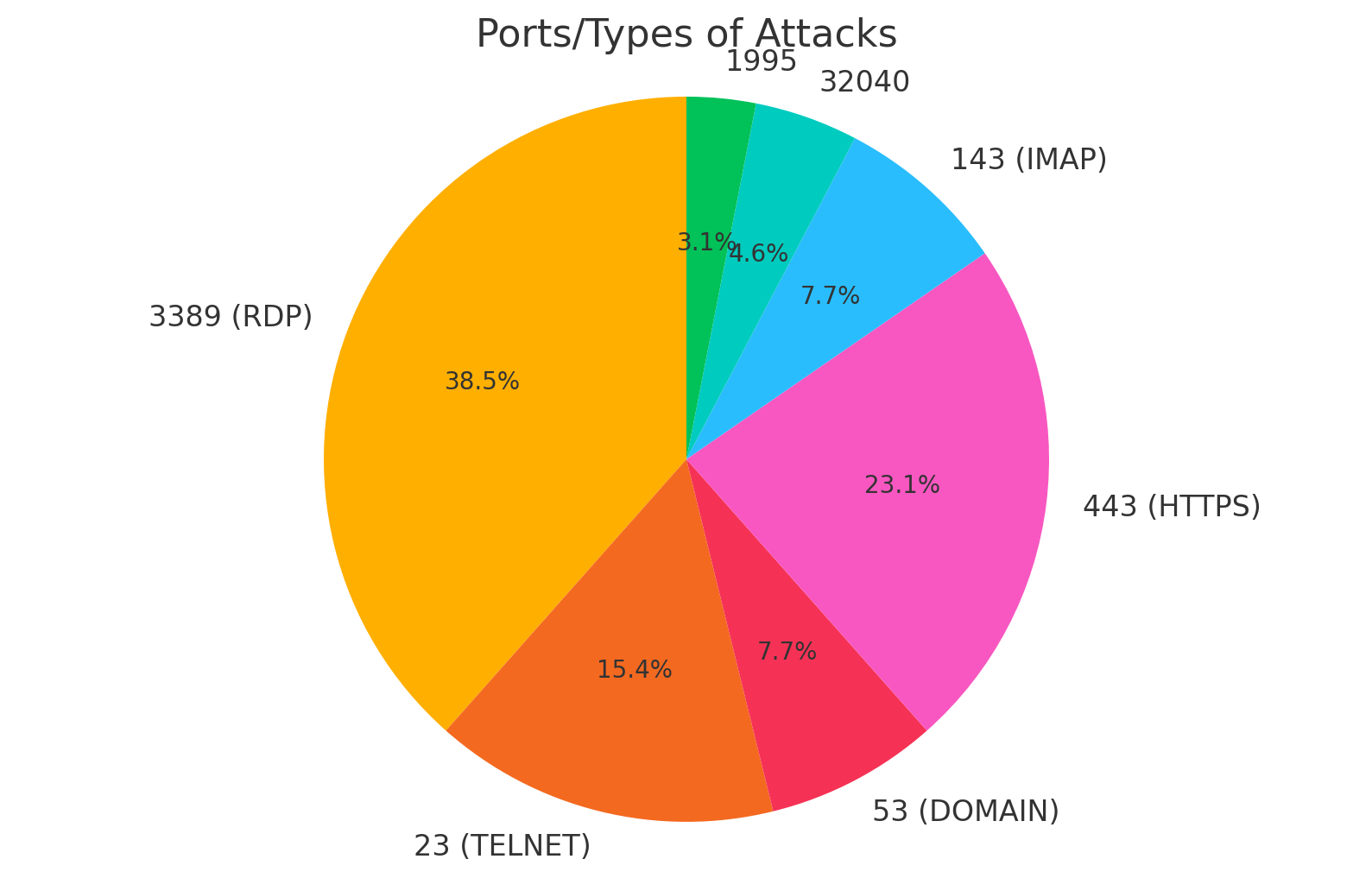
Various ports were targeted repeatedly, with a noticeable increase in attacks from within the US following the implementation of country blocks. The most attacked ports included those associated with remote desktop protocol (RDP), telnet, and various high-risk services.

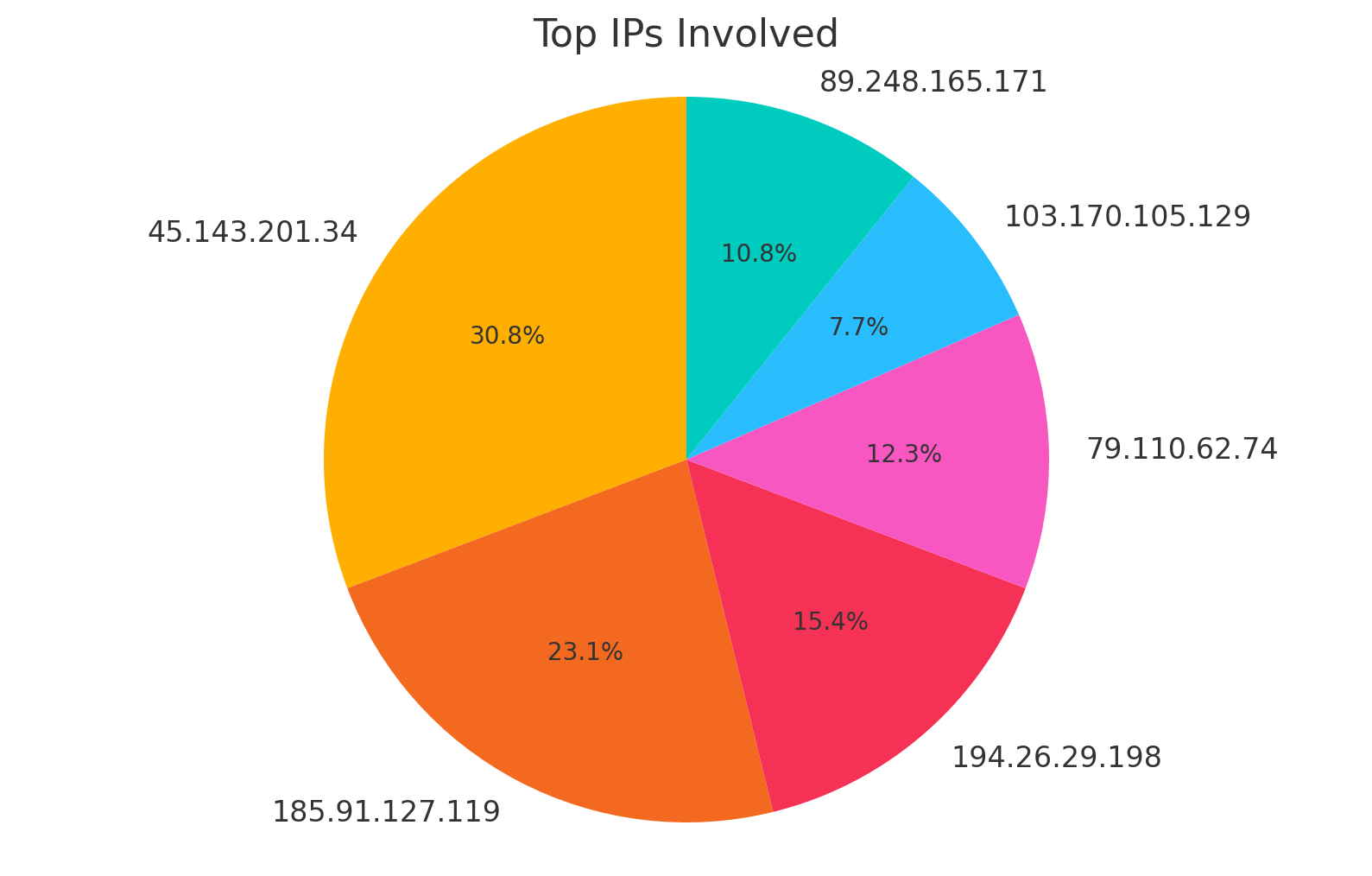
Select an IP address to learn more about it:
Select an IP address from the dropdown to see the details.
Here is the line graph showing the total number of firewall hits after installing IPFire, with data from August 7 to August 13, 2024. The trend demonstrates a significant decrease in hits over time, particularly after August 11, indicating the effectiveness of the firewall in reducing unwanted traffic.
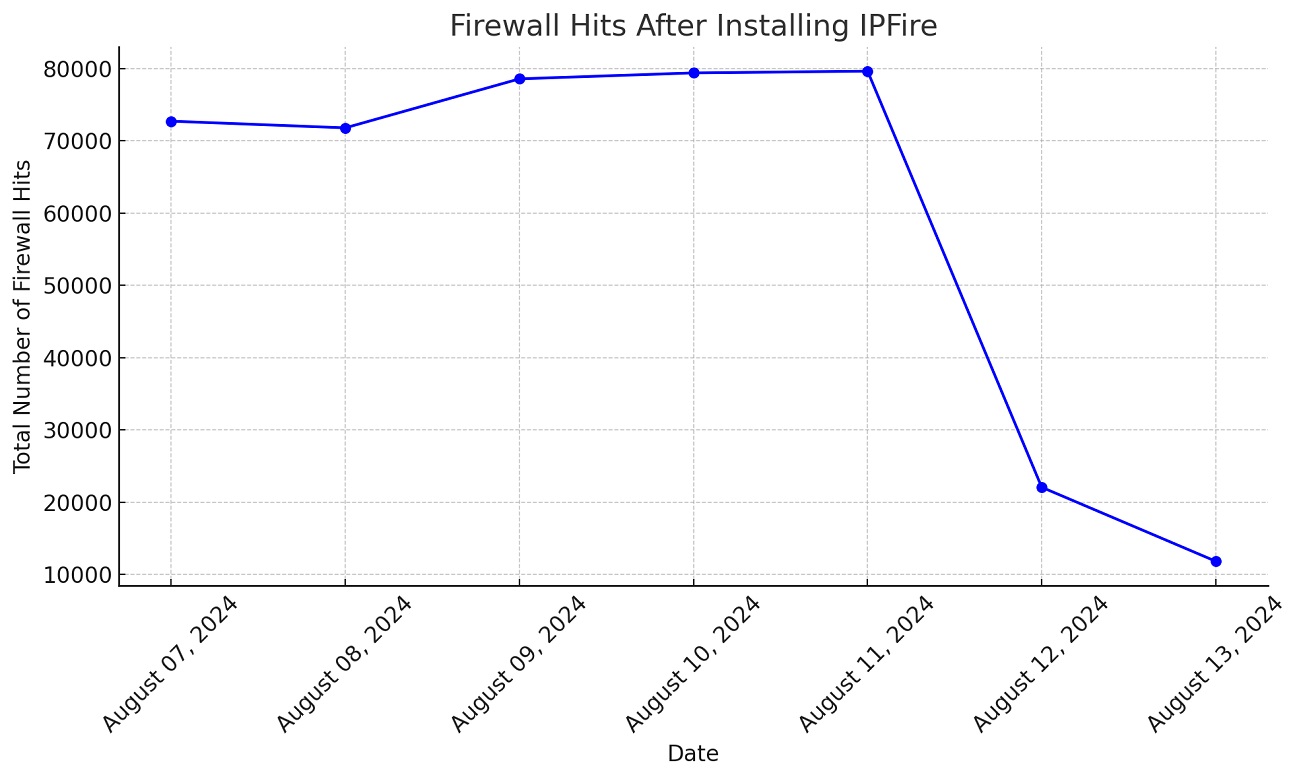
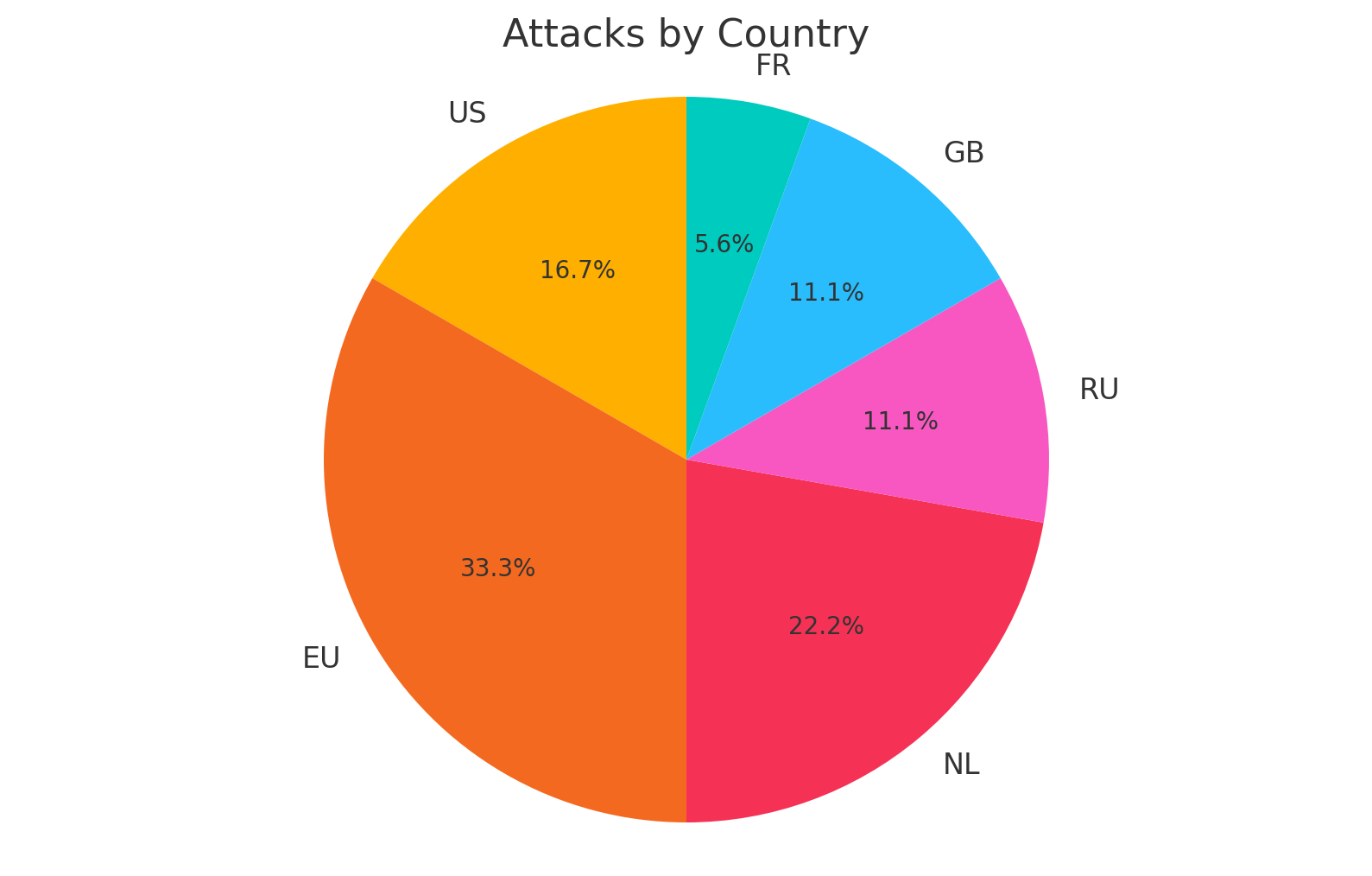
Now that most of of the global traffic has been blocked, we can see the attacks are mainly from US IP's, which should be easier to report.
While our server is now more secure, we plan to enable Intrusion Prevention System (IPS) features to further inspect and filter incoming traffic, adding an additional layer of protection. Additionally, our future security enhancements include:
For more information on securing your network with advanced firewalls, contact us today. Let's discuss how we can help protect your digital assets from cyber threats.